In simple terms, URL phishing is a fraudulent activity of imitating familiar internet links to incite victims to click on them. These links usually lead to malicious, malware-ridden sites that fish for a person’s credentials, especially banking information and passwords.
Hyperlinks in email can often connect to a web domain different from what they appear to be. Some links may display a recognizable domain name, but, in fact, direct the user to a different, malicious domain. (EDITOR’S NOTE: Users are encouraged to always review link contents by hovering the mouse pointer over the link to see if the actual link is different from the displayed link. The resources below will also aid users in making informed decisions when receiving links in emails.)
The threat actors often hide phishing website links in emails through email phishing or text messages (smishing), or other messaging apps or social media platforms. Those links are tailored to look like known brands like Twitter, Google, Microsoft, Zoom, and Amazon or governmental institutions that deal with health, finances, or social benefits.
LinkedIn Has Unique URL Phishing Vulnerabilities
The Cyberwire predicts that spear phishing attacks will increase in frequency in 2023, specifically via LinkedIn accounts. URL phishing is an excellent threat vector to execute spear phishing attacks through LinkedIn due to the fact that when user’s share a link that’s longer than 26 characters, LinkedIn will automatically shorten it once they click Post, to make it easier to read and user’s can add text to their post either before or after the URL. This coupled with what I covered above regarding links being tailored to look like know brands potentially blended with fake accounts masquerade as legitimate users and users have the potential to get smoked by threat actors.
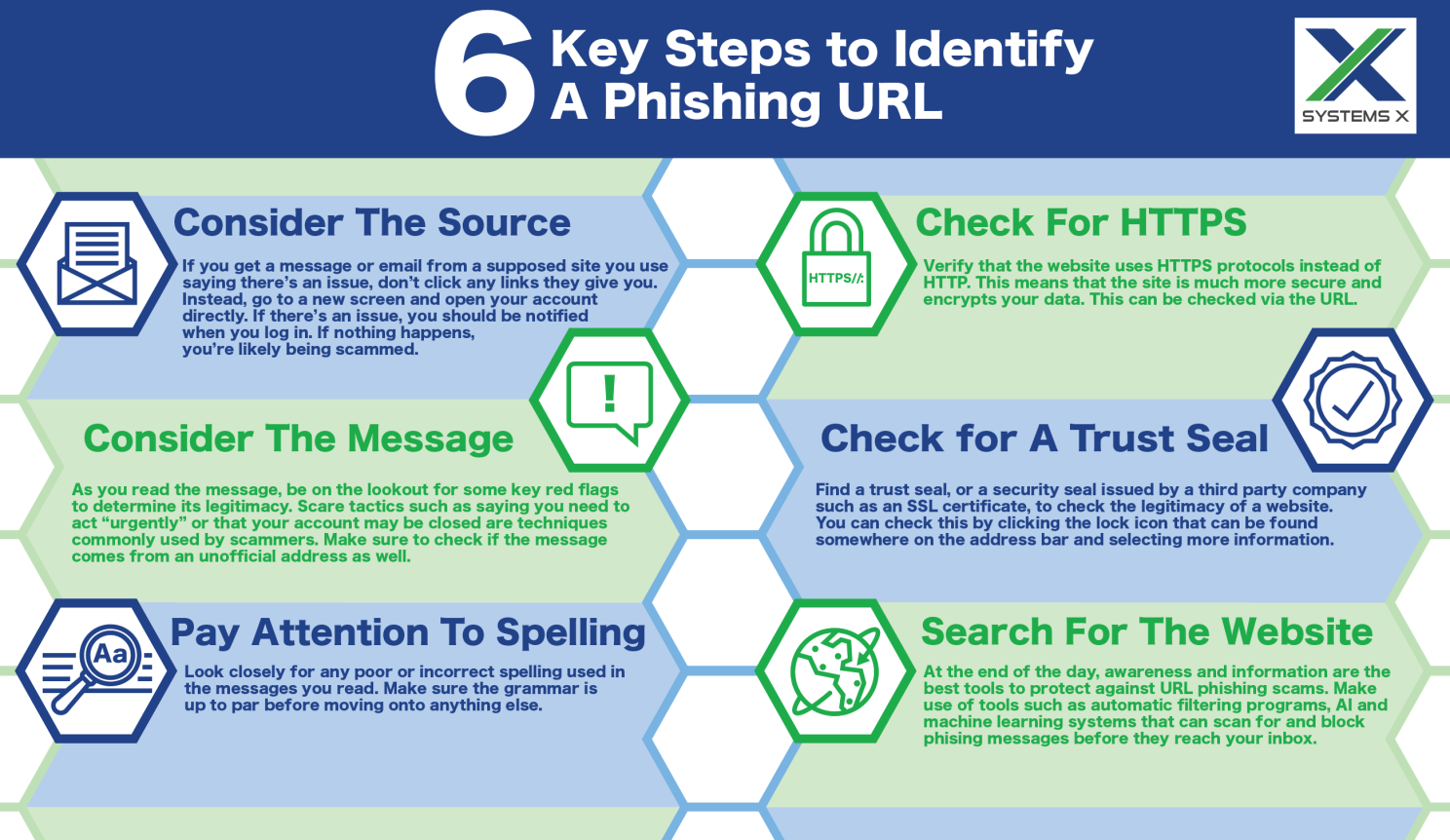
Ways To Detect URL Phishing
Traditionally, users are encouraged to always review link contents by hovering the mouse pointer over the link to see if the actual link is different from the displayed link. While that is still prudent, with URL shortening and other obfuscation techniques, this is often not enough.
Checking Shortened URLs
One clue that a link in email may be dangerous is that the URL seems too short. While link-shortening services such are popular and common tools for creating shorter links, threat actors also use link shortening to conceal their links’ true destinations. The following websites will help users in figuring out the legitimacy of shortened URLs.
URL Scanning Websites
URL scanners are websites and that let you enter the URL of a suspicious link and check it for safety. The following websites will help users in figuring out the legitimacy of shortened URLs.
Reporting URL Phishing
When it comes to reporting phishing URLs, there are several options available to users. As companies do not have one shared entity of phishing URLs but collect their own data, the first thing to do when discovering a fake URL is to let your IT staff know about it. If you do not have an IT staff, the following resources are available to take the fight to the enemy:
- Send a copy of the email to the US government-owned reporting page via CISA and have experts review your encounter.
- Provide any contents of the suspicious email to the Anti-Phishing Working Group (APWG), including the header and the body of the message.
- Report the suspicious website to Google, so they can take it down.
- Fill out the FBI’s Internet Crime Complaint Center (IC3) form if you become a victim of URL phishing.
Conclusion
As URL phishing grows as a threat vector, particularly on LinkedIn, staying informed about how you can detect URL phishing as well as how to report it will help. The resources I have listed for you will greatly reduce your chances of becoming a victim of this growing threat vector.
